Data Security Learning Module
Firewalls & Intrusion Detection Systems
Created By Eng. Eslam Osama
Security Objectives
Before diving into firewalls and IDS, it's crucial to understand the fundamental goals of information security:
Confidentiality
Protection of data from unauthorized disclosure.
Integrity
Assurance that data received is as sent by an authorized entity.
Availability
Assures that systems work promptly and service is not denied to authorized users.
Authenticity
The property of being genuine/able to be verified/trusted/confidence in the validity of a transmission/message/message originator.
Accountability
The security goal that generates the requirement for actions of an entity to be traced uniquely.
Information Security vs Network Security
Information Security
Information security means protecting data so that only the right people can access it (confidentiality), it stays accurate and unchanged (integrity), and it's available when needed (availability). It also includes user's identity can be identified (authenticity), actions can be tracked (accountability), no one can deny their actions (non-repudiation), and the system works reliably.
Network Security
Network security focuses on protecting networks and their devices from unauthorized access, changes, or damage. It ensures that data can move safely through the network and that everything connected (like routers or servers) works correctly and securely without causing harm or being exposed to threats.
Firewalls
What is a Firewall?
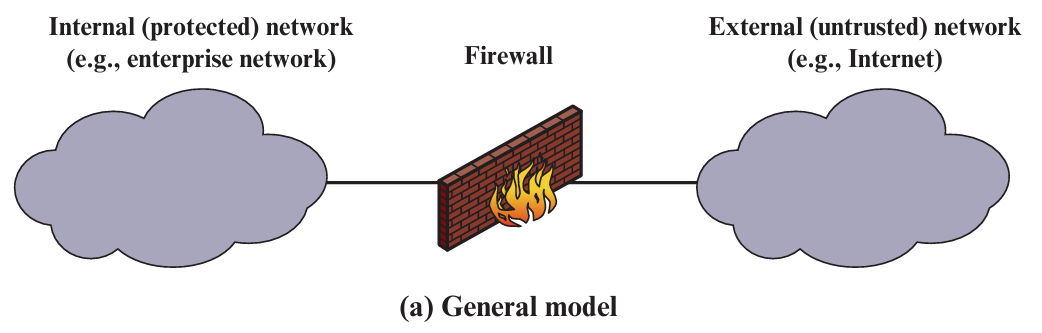
A firewall is like a security gate that controls what data can go in or out of your network. It helps protect your internal network from the dangers of the internet and is often the first layer of defense.
Main Purposes and Functions of Firewalls
Firewalls control what data enters or leaves a network by checking each packet against a set of rules. They filter traffic based on details like:
- Source IP address (where it's coming from)
- Destination IP address (where it's going)
- Port numbers (type of service like web or email)
- Protocols (like TCP or UDP)
This helps block unwanted or harmful traffic and only allows approved connections to pass through.
Firewalls help control who can access your network by using predefined rules, which are settings created by network administrators to decide what is allowed or blocked. These rules tell the firewall to either permit or deny network connections based on things like IP addresses, ports, or types of services.
NAT lets many devices (like phones, laptops, smart devices) inside your private network use one public IP address to connect to the internet.
Purpose:- Hides internal IP addresses from the outside world for extra security
- Helps the firewall control traffic coming in and going out
- You have a router/firewall with NAT
- Inside your network: devices use private IP addresses
- When devices access internet, NAT changes the private IP into the public IP of the router
- It keeps track of the requests, so when the response comes back, it knows which internal device should get it (using translation table)
Firewalls provide protection against various network threats, such as malware, viruses, and intrusion attempts.
Firewalls often support VPNs (Virtual Private Networks), which allow users to safely connect to a private network from a remote location (like from home or while traveling). A VPN encrypts the connection, keeping data private and secure from hackers, especially on public Wi-Fi. Firewalls help control and protect these remote connections by only allowing trusted users to access the network.
Firewalls maintain logs of network traffic and security events. These logs can be used for monitoring and auditing purposes.
It is a security feature that monitors network traffic to detect and stop attacks or suspicious activity in real time and also Alert admins, so they know something suspicious is happening.
Means splitting a big network into smaller, separate zones or sections using a firewall. Each section is like a "mini-network" inside the main one.
Purpose:
- Better security: Keep sensitive parts (like servers or admin systems) separate from general user traffic
- Limit damage: If a hacker gets into one zone, they can't easily move to other zones
- 1. All traffic from inside to outside, and vice versa, must pass through the firewalls.
- 2. Only authorized traffic, as defined by the local security policy and rules, will be allowed to pass.
- 3. The firewall itself is immune to penetration. This implies the use of a hardened system with a secured operating system (OS).
Types of Firewalls
1. Packet Filtering Firewall
A network security tool that checks each data packet and decides if it should be allowed or blocked, based on rules. It works on Network layer to handles IP addresses and Transport layer to handles port numbers and protocols.
Packet Filtering Firewall Diagram
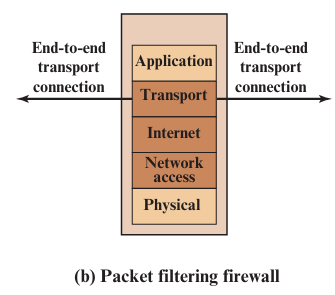
What it looks at:
- Source IP address - where the packet comes from
- Destination IP address - where the packet is going
- Port numbers - what type of service is being used (like web or email)
- Protocol - like TCP, UDP, or ICMP
Advantages
- Simple and easy to configure
- Fast and uses fewer resources
- Good for basic protection
Disadvantages
- Only checks basic info (IP, port)
- Can't see what's inside the packet content
- Can't detect complex attacks or viruses
2. Stateful Inspection Firewall
A smart type of firewall that not only looks at each packet (similar to Packet Filtering Firewall) but also remembers previous packets and the state of the connection. It works on Network layer to handles IP addresses, Transport layer to handles port numbers and protocols, and state awareness to keeps track of connection status.
Stateful Inspection Diagram
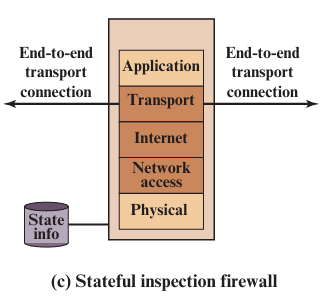
Advantages
- Smarter and more secure than basic packet filtering
- Can stop packets that are out of place or fake
- Tracks entire connections, not just individual packets
Disadvantages
- More complex to configure
- Uses more system resources
- Might slow down performance slightly in big networks
3. Application-Level Gateway (ALG)
A type of firewall that acts like a security middleman between users and web servers as it inspects and filters traffic at the Application Layer.
ALG Diagram
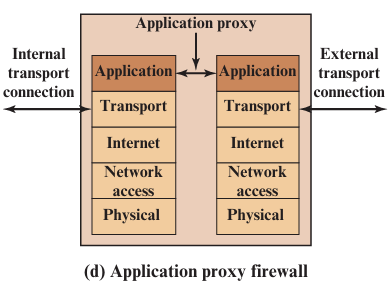
How it Works
- User sends a request (e.g., to visit a website)
- The ALG receives the request first
- It analyzes the content based on the application's protocol like HTTP
- If the content is safe, it forwards the request to the real destination
- It can block, modify, or log requests if they are harmful or restricted
Advantages
- High security -- understands app-level threats
- Can analyze data deeply (like URLs, keywords, file types)
- Can enforce policies (e.g., block certain sites, limit uploads)
Disadvantages
- Slower than other firewalls because of deep inspection
- More complex to set up and manage
- Not suitable for untrusted external communications
4. Circuit-Level Gateway
A type of firewall that works at the Transport Layer to control network connections. It doesn't inspect the content of traffic, just makes sure the connection (like a TCP handshake) is valid.
Circuit-Level Gateway Diagram
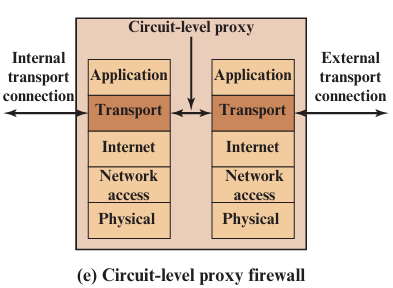
How it Works
- A user inside the network wants to connect to an outside server (e.g., a website)
- The Circuit-Level Gateway creates two connections:
- One between the user and the gateway
- One between the gateway and the external server
- The gateway forwards traffic between both connections
- It monitors the session setup only, not the actual data
Advantages
- Faster than deep-inspection firewalls
- Low resource use -- doesn't slow down the network
- Simple setup, ideal for trusted internal users
Disadvantages
- Doesn't inspect data -- can't detect malware or harmful content
- Not suitable for untrusted external communications
Demilitarized Zone (DMZ) Networks
What is a DMZ?
A DMZ (Demilitarized Zone) is a special zone in a network that sits between the internal network (LAN) and the external internet (WAN). It acts as a buffer zone for hosting public services (like websites) while protecting the internal network.
DMZ Network Diagram
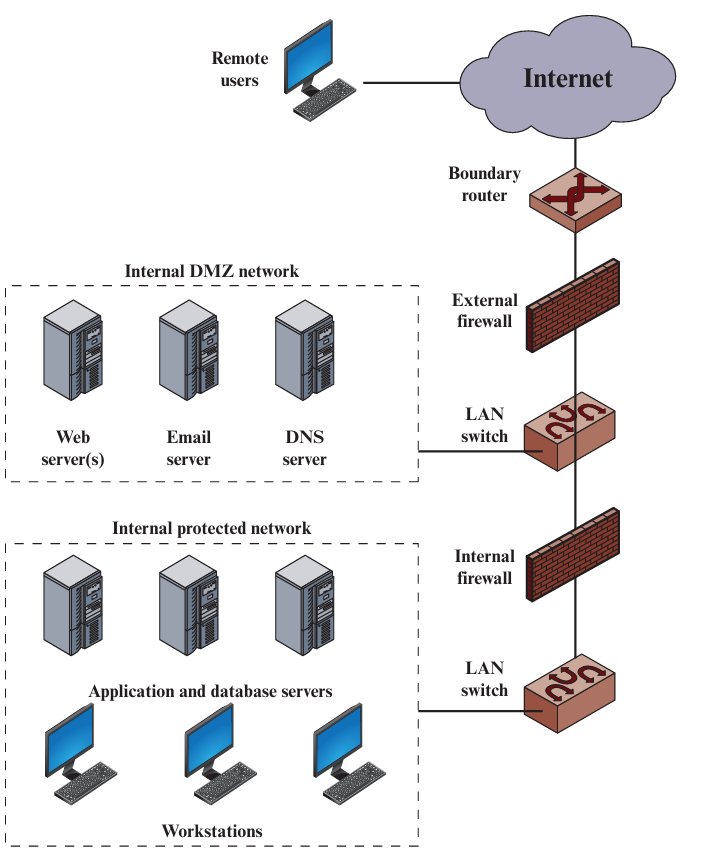
Purpose of DMZ
- To host public services (that anyone on the internet can access), without exposing the entire internal network to risks
- If someone attacks a server in the DMZ, they still can't reach the sensitive internal network directly
Benefits of DMZ
- Adds an extra layer of protection between public services and internal systems
- Allows safe public access to things like company websites or email servers
- Keeps private resources hidden from external threats
Typical DMZ Services
Web Servers
Host company websites accessible to the public
Email Servers
Handle incoming and outgoing email communications
DNS Servers
Resolve domain names for external users
FTP Servers
Allow file transfers with external parties
Intrusion Detection Systems (IDS)
What is an IDS?
It is a hardware or software solution that monitors, gathers, and analyzes information from a computer system or network to detect and alert about unauthorized or suspicious attempts to access, misuse, or compromise system resources.
Key Functions: Monitoring, Detecting, and Alerting
Note: IDS is a passive system as it does not block attacks, only detects and alerts.
What is an Intrusion?
Any violation of security policies, whether by external attackers or internal authorized users, that threatens:
- Confidentiality (unauthorized access to data)
- Integrity (unauthorized modification of data)
- Availability (disruption of service)
What is Intrusion Detection?
The process of monitoring and analyzing system or network activities to identify signs of intrusions or policy violations.
Types of Intrusion Detection Systems
Host-Based IDS (HIDS)
Monitors activities on individual devices like computers or servers as it keeps an eye on system files, logs, and applications to spot any unusual behavior or unauthorized changes.
Example: If someone tries to alter important system files on a web server, HIDS will detect this and alert the administrator.
Network-Based IDS (NIDS)
Watches over the entire network's traffic to identify suspicious activities as it analyzes data packets moving across the network to detect patterns that match known threats or anomalies.
Example: DOS attack on the service server in the network, NIDS will recognize this and send an alert to firewall to stop these requests.
IDS Logical Components
Sensors
Responsible for collecting data from various sources in the system or network.
Analyzers
Receive input from sensors and are responsible for determining if an intrusion has occurred.
User Interface
Enables a user to view output from the system or control its behavior.
IDS Detection Techniques
1. Misuse Detection (Signature-Based)
Compares incoming data to a database of known attack patterns (signatures). If a match is found, an alert is triggered.
Analogy
Like a security guard checking IDs against a list of known criminals.
Advantages
- Quick and accurate detection of known threats
- Low false positive rates
Disadvantages
- Cannot detect new or unknown attacks
- Requires regular updates to the signature database
2. Anomaly Detection
Establishes a baseline of normal system behavior and flags deviations from this norm as potential threats.
Analogy
Like a bank noticing unusual spending patterns on your credit card.
Advantages
- Can detect new or previously unknown attacks
- Adaptable to changing network behaviors
Disadvantages
- Higher false positive rates due to normal behavior variations
- Requires a learning period to establish accurate baselines
IDS Performance Metrics
This is a critical concept for evaluating the effectiveness of any detection system, illustrated by the potential overlap in behaviors:
Intruder vs Authorized User Behavior Diagram
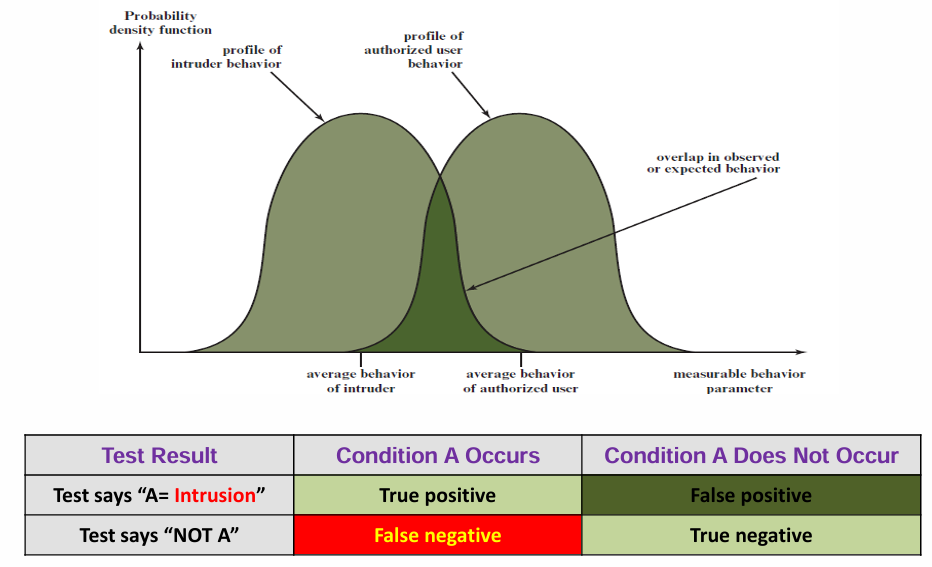
True Positive (TP)
The IDS correctly identifies an actual intrusion. (Good!)
False Positive (FP)
The IDS incorrectly flags legitimate activity as an intrusion. (Bad)
False Negative (FN)
The IDS fails to detect an actual intrusion. (Very Bad - A real attack goes unnoticed)
True Negative (TN)
The IDS correctly identifies legitimate activity as not an intrusion. (Good!)
Review Questions
Test Your Knowledge
Q1) List three design goals for a firewall?
- All traffic from inside to outside, and vice versa, must pass through the firewalls
- Only authorized traffic, as defined by the local security policy and rules, will be allowed to pass
- The firewall itself is immune to penetration
Q2) List four techniques used by firewalls to control access and enforce a security policy?
- Service control: Decides which Internet services are allowed
- Direction control: Controls whether service requests can flow into or out of the network
- User control: Controls access according to which user is attempting to access it
- Behavior control: Manages how certain services are used
Q3) What information is used by a typical packet filtering firewall?
- Source IP address - where the packet comes from
- Destination IP address - where the packet is going
- Port numbers - type of service being used
- Protocol - like TCP, UDP, or ICMP
Q4) What are some weaknesses of a packet filtering firewall?
- Only checks basic information (IP addresses, ports)
- Cannot see what's inside the packet content
- Cannot detect complex attacks or viruses
- No context awareness of connection state
Q5) What is the difference between a packet filtering firewall and a stateful inspection firewall?
Packet Filtering Firewall: Only examines individual packets based on basic criteria (IP addresses, ports, protocols) without considering the connection context.
Stateful Inspection Firewall: Not only examines individual packets but also remembers previous packets and tracks the state of connections, making decisions based on the entire connection context.
Q6) What is an application-level gateway?
A type of firewall that acts as a security middleman between users and web servers, inspecting and filtering traffic at the Application Layer. It analyzes the actual content of communications based on application protocols like HTTP, rather than just examining packet headers.
Q7) What is a circuit-level gateway?
A type of firewall that works at the Transport Layer to control network connections. It doesn't inspect the content of traffic, but ensures that connections (like TCP handshakes) are valid by creating separate connections between the user-gateway and gateway-external server.
Q8) What is a DMZ network and what types of systems would you expect to find on such networks?
DMZ (Demilitarized Zone): A special network zone that sits between the internal network and the external internet, acting as a buffer zone for hosting public services while protecting the internal network.
Typical systems in DMZ:
- Web servers
- Email servers
- DNS servers
- FTP servers
- Public-facing application servers
Q9) What is the difference between an internal and an external firewall?
External Firewall: Sits between the external internet and the DMZ/internal network, protecting against outside threats and controlling what external traffic can enter the network.
Internal Firewall: Sits between the DMZ and the internal network, providing an additional layer of security to protect sensitive internal resources from both external threats and potentially compromised systems in the DMZ.
Q10) Explain the difference between host-based and network-based intrusion detection systems?
Host-Based IDS (HIDS): Monitors activities on individual devices (computers, servers) by examining system files, logs, and applications to detect unauthorized changes or suspicious behavior on that specific host.
Network-Based IDS (NIDS): Monitors the entire network's traffic by analyzing data packets moving across the network to detect suspicious activities, attack patterns, or anomalies in network communications.
Q11) What are the main logical components of an IDS?
- Sensors: Responsible for collecting data from various sources
- Analyzers: Receive input from sensors and determine if an intrusion has occurred
- User Interface: Enables users to view output from the system or control its behavior
Q12) What are the two main approaches to intrusion detection?
- Misuse Detection (Signature-Based): Compares incoming data to a database of known attack patterns (signatures) and triggers alerts when matches are found.
- Anomaly Detection: Establishes a baseline of normal system behavior and flags deviations from this norm as potential threats.